In the latest storm to rock the global spyware industry, Intellexa—the embattled maker of the Predator spyware—has been accused of remotely accessing the surveillance systems of its own government clients, peering directly into the lives of those being targeted. This revelation, unearthed by Amnesty International and a coalition of investigative journalists, is not just another notch in the spyware scandal belt. It’s a seismic shift in the balance of power and trust between spyware vendors, governments, and the privacy expectations of billions of people worldwide.
Why This Matters
- This goes beyond government overreach. For the first time, a private spyware vendor may have had live access to espionage operations, fundamentally challenging the industry’s claimed ‘Chinese wall’ between vendor and customer.
- It exposes a privacy nightmare. Victims are now not only vulnerable to government surveillance, but also to a foreign company with dubious security practices.
- It’s a red flag for international relations. With government agencies potentially unwittingly sharing sensitive intelligence with an overseas company, the risks of leaks, blackmail, or misuse skyrocket.
What Most People Miss
- The technical smoking gun: The leaked training video, allegedly showing TeamViewer sessions into live government surveillance dashboards, contains specific infection attempts—right down to URLs, IP addresses, and device info. This isn’t generic training; it’s real, actionable data.
- Industry contradiction: While Intellexa’s competitors (like Memento Labs and NSO Group) insist on a strict hands-off policy once their malware is delivered, Intellexa appears to have violated the industry’s core red line.
- Legal and diplomatic fallout: Such access could make Intellexa directly liable for illegal surveillance, and could expose governments to international embarrassment or compromise ongoing operations.
- Shaky trust between partners: If governments can’t trust their vendors, will they pull back from using these tools, or double down on secrecy and home-grown solutions?
Key Takeaways
- Intellexa allegedly kept a backdoor into government spyware operations—a move that breaks every supposed rule of the spyware trade.
- Victims of Predator spyware are now twice-exposed: first to their own governments, second to a foreign, for-profit entity.
- This revelation casts doubt on oversight claims: If vendors can see everything, who is watching the watchers?
Context: How Did We Get Here?
- Spyware boom: The past decade has seen governments worldwide quietly contracting with private spyware vendors, using tools like Pegasus (NSO Group) and Predator (Intellexa) to target criminals, journalists, dissidents, and sometimes political rivals.
- US sanctions: In 2024, the US government sanctioned Intellexa’s founder Tal Dilian and partner Sara Hamou for allegedly targeting Americans—including government officials and journalists—with Predator spyware.
- Industry denial: Vendors have long claimed they only sell the tools—they don’t operate them, see the data, or know who’s targeted. This Intellexa leak shatters that narrative.
Pros and Cons: Remote Vendor Access
- Pros (from a vendor perspective):
- Easier troubleshooting and support
- Ability to update or patch systems remotely
- Cons (for governments and victims):
- Loss of control over sensitive operations
- Potential for data leaks or vendor misuse
- Legal and diplomatic exposure
Expert Commentary
“No [government] agency would accept it,” said Paolo Lezzi, CEO of rival Memento Labs, emphasizing how extraordinary Intellexa’s alleged access is compared to industry norms.
“Not only is their most sensitive data exposed to a government or other spyware customer, but their data risks being exposed to a foreign surveillance company, which has demonstrable issues in keeping their confidential data stored securely.” — Amnesty International
Tal Dilian, Intellexa’s founder, fired back at critics, blaming an “orchestrated campaign” of journalists and the Biden administration, but stopped short of addressing the specifics of the leaked video.
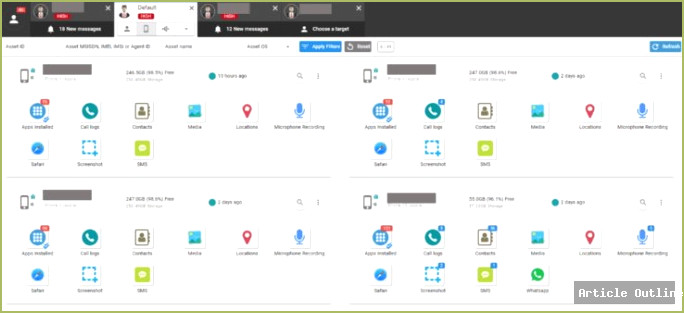
Timeline: Intellexa, Predator, and Global Fallout
- 2019-2022: Predator spyware emerges as a competitor to NSO’s Pegasus, quickly gaining infamy for targeting journalists and activists globally.
- 2024: US sanctions Intellexa’s leadership for alleged attacks on Americans.
- December 2025: Amnesty and partners release leaked material showing live vendor access.
The Bottom Line
If true, these revelations obliterate the last pretense of control governments have over their digital espionage—and double the danger for anyone targeted by state surveillance. It’s a wake-up call for policymakers, investigators, and everyday citizens: The spyware industry isn’t just a government problem—it’s a global, private-sector risk with few guardrails and even fewer consequences.
Action Steps
- Governments must demand absolute transparency and independent audits from spyware vendors.
- International organizations should push for enforceable regulations on the export and operation of surveillance tools.
- Potential victims—especially journalists, activists, and politicians—should adopt robust digital hygiene and seek independent security audits.